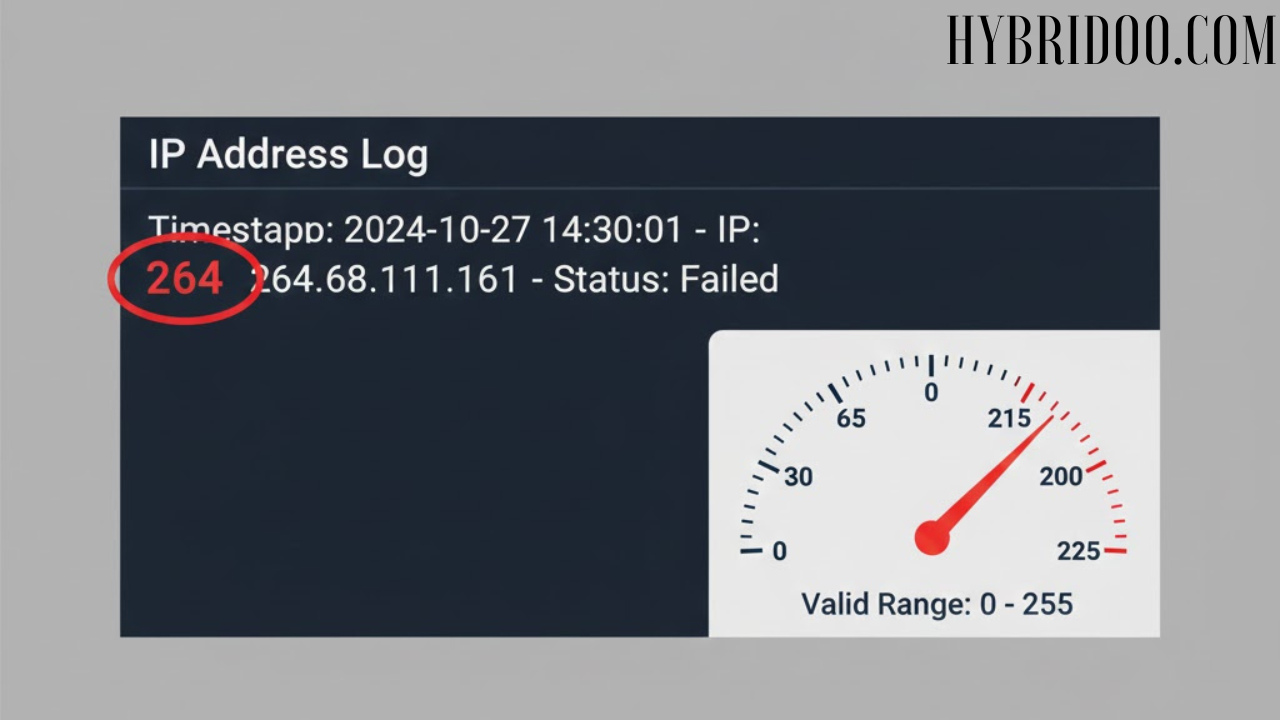
In the intricate web of the internet, where billions of devices connect and communicate daily, IP addresses serve as the fundamental digital identifiers. Occasionally, a sequence like 264.68.111.161 surfaces in logs or documentation, sparking curiosity and sometimes concern. However, a closer technical examination reveals a critical fact: 264.68.111.161 is not a valid IP address. Understanding why this is the case offers a valuable lesson in networking fundamentals, data validation, and cybersecurity vigilance.
Understanding IP Addresses: The Internet’s Digital Coordinates
Before dissecting the specific case of 264.68.111.161, it’s essential to grasp what an IP address is and how it functions.
-
Core Function: An Internet Protocol (IP) address is a unique numerical label assigned to every device connected to a network. It enables the precise routing of data packets across the globe, functioning much like a postal address for digital communication.
-
IPv4 Structure: The most common format, IPv4, uses a 32-bit address expressed as four decimal numbers (called octets) separated by periods (e.g., 192.168.1.1). Each octet represents 8 bits of data.
-
The Fundamental Rule: Due to this 8-bit structure, the value of each octet in an IPv4 address must fall within the range of 0 to 255. This is a non-negotiable standard of internet protocol.
The Technical Breakdown: Why 264.68.111.161 Fails
The invalidity of 264.68.111.161 becomes immediately apparent when we apply the fundamental rule of IPv4 addressing.
Let’s examine its structure:
| Octet Position | Value in 264.68.111.161 | Valid Range (0-255) | Status |
|---|---|---|---|
| First Octet | 264 | 0 – 255 | INVALID |
| Second Octet | 68 | 0 – 255 | Valid |
| Third Octet | 111 | 0 – 255 | Valid |
| Fourth Octet | 161 | 0 – 255 | Valid |
The first octet, with a value of 264, exceeds the maximum allowable value of 255. In binary terms, 8 bits cannot represent a number this high. Consequently, 264.68.111.161 is a non-routable, non-functional address. It cannot be assigned to any device on the public internet, and attempts to ping it, trace it, or visit it will fail.
Common Contexts Where You Might Encounter This Invalid Address
Despite being technically inert, this address string can appear in various places, often as an anomaly or a tool:
-
System Logs and Errors: As a result of human typographical errors, misconfigured scripts, or software bugs during data generation.
-
Educational and Testing Material: Developers and educators frequently use obviously invalid addresses like this one as safe placeholders in code examples, documentation, or network simulations to avoid accidentally referencing real systems.
-
Cybersecurity Analysis: Malware or malicious scripts may contain invalid IPs to obfuscate their code or test system responses. Security researchers might also use them in honeypots—deceptive systems designed to attract and study attackers.
Security Implications: Is 264.68.111.161 a Threat?
On its own, the address poses no direct threat; you cannot connect to it, and it hosts no malicious server. However, its presence in your network environment should not be blindly ignored, as it can be an indicator of underlying issues.
-
Symptom of a Larger Problem: Its appearance in logs could point to misconfigured network equipment, flawed application logic, or poor data hygiene that might mask other vulnerabilities.
-
Potential for Obfuscation: In cybersecurity, invalid IPs can be used in IP spoofing attempts, where attackers forge packet headers to hide their true origin or bypass basic filtering rules. While a sophisticated attacker would use a valid-but-fake IP, malformed ones can sometimes slip through to probe a system’s validation robustness.
-
Signal for Investigation: A single instance might be a typo, but repeated occurrences, especially in security logs, warrant a closer look to rule out automated probing or attack fuzzing.
Best Practices: How to Handle and Prevent Invalid IPs
Proactive management is key to maintaining clean data and a secure posture. Here’s what IT professionals, developers, and system administrators should do:
-
Implement Rigorous Input Validation: Ensure every system that accepts an IP address validates its format. Checks should confirm there are four octets and that each octet is a number between 0 and 255. Use established libraries for this task rather than writing custom validation from scratch.
-
Automate Log Monitoring and Filtering: Deploy tools or scripts that automatically scan logs and flag entries containing malformed IP addresses. This helps in early detection of misconfigurations or suspicious activity.
-
Establish Clear Development Protocols: Mandate the use of official reserved IP ranges for testing and documentation (e.g., which is designated for examples). This prevents fictional addresses like 264.68.111.161 from being used in code that might later reach production.
-
Educate Your Team: Foster awareness about basic IP address structure across development and operations teams. A team that understands why
264.68.111.161is invalid is better equipped to prevent and troubleshoot related issues. -
Maintain a Strong Security Posture: Equip firewalls and intrusion detection/prevention systems (IDS/IPS) to scrutinize traffic for anomalies, including patterns that might involve spoofed or malformed addresses.
The Bigger Picture: IPv4, IPv6, and the Future of Addressing
The limitation that makes 264.68.111.161 invalid stems from the finite space of IPv4 (approximately 4.3 billion addresses). This exhaustion has driven the global transition to IPv6.
-
IPv6’s Vast Space: IPv6 uses a 128-bit address, allowing for an essentially limitless number of unique addresses.
-
Different Structure, Different Rules: While an address like 264.68.111.161 has no place in IPv4, the segmented, hexadecimal notation of IPv6 operates under entirely different validation rules. The core lesson remains: understanding protocol standards is crucial.
Key Takeaways at a Glance
-
264.68.111.161 is invalid because its first octet (264) exceeds the maximum IPv4 value of 255.
-
It cannot route traffic or be assigned to a real device on the internet.
-
It may appear due to human error, as a testing placeholder, or within security logs.
-
While not directly harmful, it can be a red flag for misconfiguration or poor data validation.
-
Defend your systems by validating all IP inputs, monitoring logs, and using proper testing address ranges.
The story of 264.68.111.161 is more than a technical footnote. It underscores a critical principle in technology and security: understanding the rules of the system is the first step toward controlling it. By demystifying this invalid address, we reinforce the importance of fundamentals, vigilance, and precision in building and maintaining a reliable digital world.
Have you encountered puzzling entries in your network logs? Start by auditing your current logging and validation systems. Ensure your team is trained on these networking fundamentals, and consider implementing a review of how IP addresses are handled in your applications. A proactive approach to these small details is a cornerstone of robust IT infrastructure and cybersecurity.